The two previous articles discussed the ethical and practical motivations behind Jami’s distributed architecture. As we have seen, this design brings many advantages including privacy, autonomy, scalability and resilience, but they come at a cost. This week, we will explore the challenges that are inherent to Jami’s distributed architecture and the solutions that we came up with to surmount them.
Paul Baran’s definition of a distributed network (illustration bellow) refers to the absence of a central server who relays all the messages between peers. Most modern communication systems are decentralized, or somewhere in between centralized and distributed, where multiple servers are present. Jami is completely distributed, meaning there is no central authority at all in the network and the communications are completely peer to peer. This gives users full ownership and control over their data and who they share it with without requiring them to trust a central authority.
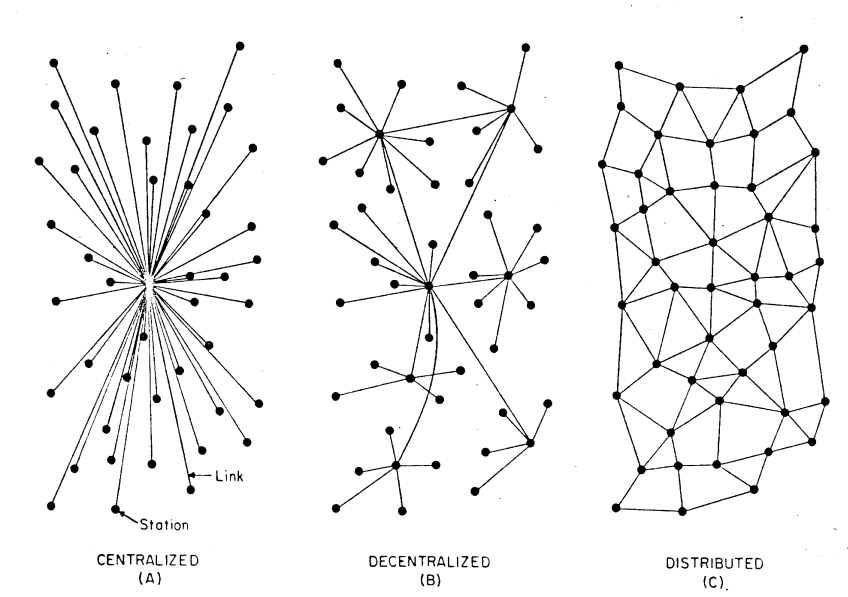
There is a good reason for the fact that most communication networks rely on servers to relay messages between users. It simplifies many aspects of the design and removing them creates technical difficulties. The main ones are listed bellow along with a short explanation and the solutions that we use for Jami.
Authentication
Traditional architectures allow for a central registry of user credentials that provide authentication functionalities. This is not possible on Jami. Instead, we use public-key cryptography to give users the ability to authenticate each other by themselves.
Solution : Public-key cryptography/ infrastructure
Identity management
We use public-key cryptography to authenticate users. However, this long string of characters is rather impractical for humans to remember. They need to be associated with a unique username for users to be able to recognize their friends on the network. The only way to avoid duplicate usernames is to rely on a central authority to manage them. In order to keep Jami fully distributed, we chose to use an Ethereum blockchain smart contract for this task.
Solution : Blockchain
Discovery
Electronic devices need to know each other’s IP address in order to communicate on the internet. When communicating with a server, its IP address is either known, or linked to a domain name that points to it. However, since Jami users communicate directly with each other and their IP address is dynamic, we need to rely on OpenDHT to establish the connection. It is a technology that we developed internally allowing devices to discover each other on the internet.
Solution : OpenDHT
Asynchronous communications
When a message is sent to someone who is disconnected, it is typically saved on a server and transmitted to them later. This is not possible on Jami. Instead, the sender’s device automatically tries to resend the message when the receiver gets back online. While this is useful, it is not a perfect solution because both users still have to be online at the same time in order for messages to be transmitted.
Solution : Resend messages when receiver is online
Account persistence
When users have full control over their data, they also have the responsibility to make sure they keep it safe. On Jami, data lives only on users’ devices and if they lose it, they may never be able to access their account again. This is why we created a way to make a backup of the account’s private key archive. It is a compressed file containing everything users need in order to recover their account in case they lose it. Another way to mitigate the risks of losing access to an account is to connect multiple devices to it.
Solution : Multiple devices or private key archive backup
NAT traversal
Servers are designed to handle millions of requests regularly and be easily accessible by anyone on the net. Jami users however, are usually connected to the Internet through a router that blocks most ports in order to protect them from hackers. This is safer, but it also creates an obstacle for establishing peer to peer connections. Jami relies on Interactive Connectivity Establishment (ICE) in order to resolve this problem.
Solution : ICE
This concludes our short series of articles on the beneficial and challenging implications of Jami's distributed architecture. We made this design decision because we believe the ethical and practical benefits outweigh the costs of surmounting the challenges mentioned above.
By François Naggar-Tremblay – Jami Product Manager








